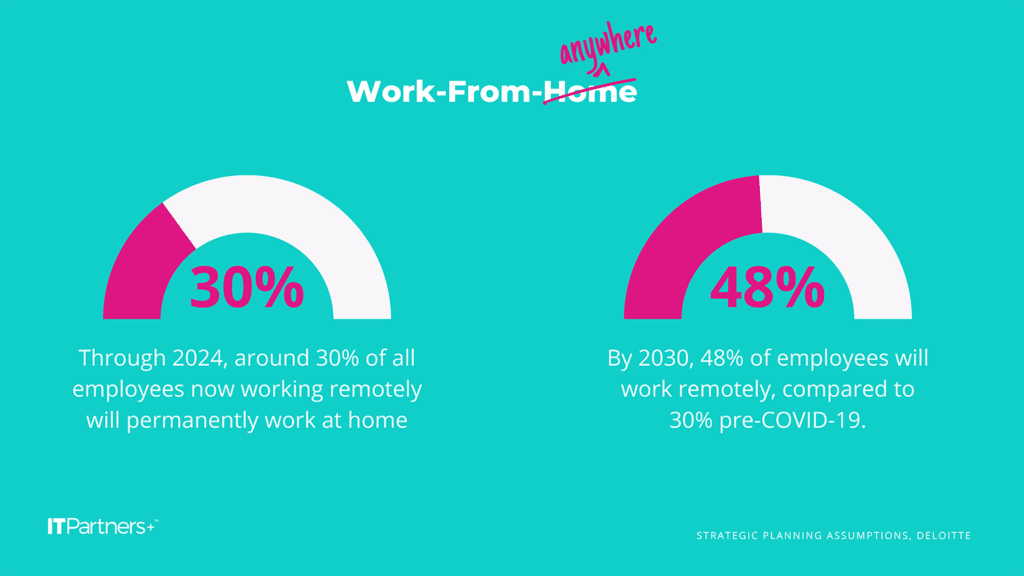
Before 2020, roughly 5% of Americans worked from home, but the pandemic brought significant changes to how and where we work… it’s now being reported that roughly 25% of the American workforce works remotely and that half of the American workforce still wishes to work from home. That’s not even counting teams with hybrid schedules!
This presents the question – are organizations prepared for the cybersecurity implications of their staff working from home? It’s tricky to manage remote workers since they are not part of the network infrastructure at the office. Many traditional perimeter and endpoint strategies for securing the environment no longer work.
In this article we’ll be covering:
- VPN
- Roaming DNS Filtering
- Secure Passphrase
- Multi-Factor Authentication
- Password Manager
- WIFI Security
- End User Education
- Detect and Respond
- Business Continuity
- Shared Responsibility
Tip #1: Install a VPN
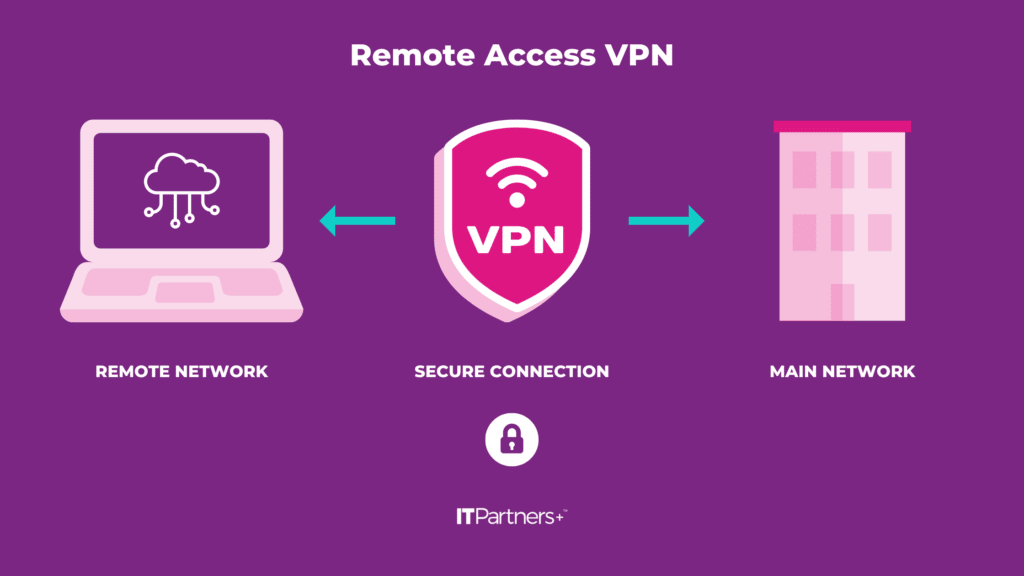
A VPN is a tried-and-true way to establish a secure connection between two networks using the Internet. This will allow the remote network to be an effective part of the main network back at the office, thereby mitigating many of the perimeter problems encountered with remote workers.
You can choose to connect the two networks together, making all devices on the remote network accessible or just an endpoint, rendering only that endpoint accessible.
Tip #2: Enable Roaming DNS Filtering
DNS filtering or DNS blocking is a security measure used to stop internet users from accessing unapproved websites on a server. It is an effective and portable way to protect both your network and individual users. Even when users are away from the network with a company device, DNS filtering can block access to malicious websites and landing pages.
Tip #3: Switch to Secure Passphrases
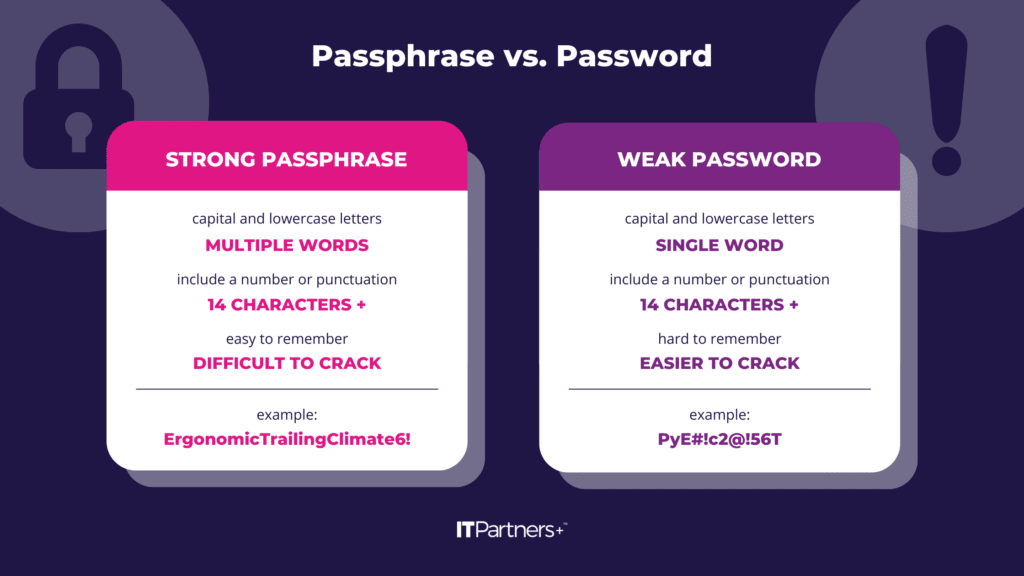
There has been some debate about which method, password, or passphrase is more secure, but, where available, passphrases are the preferred method of authentication. Secure passwords were a staple security requirement long before remote work hit the scene, but remote workers have put a spotlight on all layers of security. As one of the most basic security measures, it is often overlooked, yet still important.
Passphrases have become popular as a more secure form of username/password-type authentication, something that is somewhat easily remembered, but difficult to guess or crack. It is easier for a user to remember a passphrase like “ErgonomicTrailingClimate6!” than to remember a password like “PyE#!c2@!56T” and the passphrase is more secure. Some applications and operating systems will even allow spaces so the passphrase is more easily remembered and typed.
Tip #4: Require Multi-Factor Authentication
This method of authentication is becoming increasingly important in the security toolbox of businesses around the globe. With passwords easily guessed or easily outright stolen via phishing attempts, MFA was designed as a more secure method of authentication, to be used in conjunction with traditional username/password pairs. While not foolproof, when implemented and used properly, it is extremely effective in preventing unauthorized account access.
MFA involves the use of a token of authentication separate from a username and password. It can be a code delivered via text, phone, or email or be pushed to the user via an app on their smartphone. The token delivered via an app is more secure.
Tip #5: Utilize a Password Manager
Using a password manager will help users to adhere to the two most fundamental rules behind passwords and passphrases: make each one unique and make it strong. Many times, the end user will choose a simple password or passphrase so it is easier to remember. Passphrases help with this but are not a complete answer.
Without a way to easily manage passwords, many end users will fall back on old habits and use weak passwords or repeat the use of the same password or passphrase.
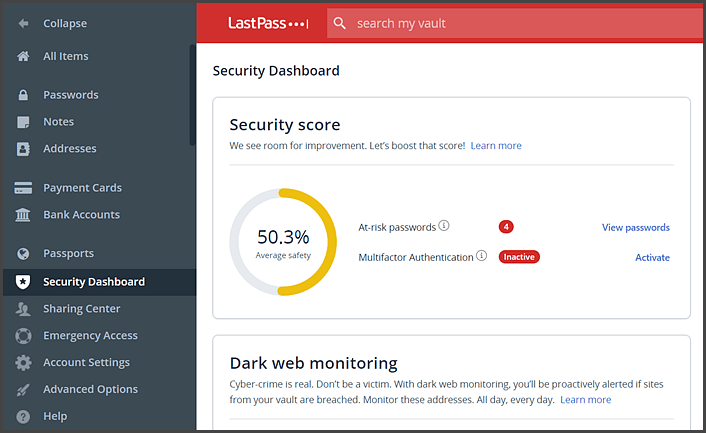
A password manager, such as LastPass, will alert the user where they have stored repeat passwords and prompt them to change the re-used password. Further, it will require a very strong password to get into the vault of passwords and will make storing the passwords easy through a browser extension. Storing your passwords in a password-protected Excel spreadsheet is NOT a password manager!
Tip #6: Review WIFI Security Protocols
Wireless networks are so ubiquitous today that it might be easy to forget the security behind them. Many companies are using old standards like WEP or WPA and don’t realize these older standards leave their network open for attack. WIFI password strength applies here as well, just as with individual user accounts.
Certainly, when users move to remote work, the wireless network gets even less thought.
For companies that have compliance requirements or those simply seeking a higher level of security for on-premise and remote networks, here are some basic recommendations:
- Make sure you are using the latest security protocol and standards. The latest security protocol for WIFI networks is WPA3.
- Make sure the password is changed periodically.
- Or better yet, tie authentication to your network directory. Whenever an employee leaves, it represents a risk to your wireless network.
Tip #7: Require Employee Training
End-User education is the last line of defense in a security plan. If all other layers of security are defeated, the end user, when properly educated, can be a formidable foe. It’s the most important piece when dealing with remote users and disparate levels of security.
Here are some highlights:
- If you receive a suspicious email, do not reply or click any links or open any attachments. Tag it for your IT team to review. The same advice applies to text messages.
- If you receive an MFA token for one of your accounts and you are not attempting a login, do not authorize access.
- If you receive a call asking you to authorize access, ignore it.
Tip #8: Upgrade EDR (Endpoint Detection and Response) Tools
Traditional anti-virus programs like McAfee, Webroot, ESET, or Symantec aren’t up to the task of providing proper detection of zero-day attacks. Further, response to an actual event needs to be targeted and swift and these products are unable to provide that level of detection or response.
A next-generation anti-virus like Cynet or Sentinel One is the preferred method of protection these days.


And better yet, back those Endpoint Detection and Response (EDR) tools with a 24×7 Security Operations Center (SOC). This will help automate many of the responses to false positives and give the around-the-clock help today’s security landscape and remote users require.
Tip #9: Update Business Continuity Strategy
Many companies navigated remote work and didn’t really modify their business continuity strategy. This could be problematic since many times, proper file backup and availability require the end user to be in the corporate domain. Further, what happens if the end-user computer dies? If it’s not a company asset, it’s likely there isn’t a plan in place.
IT departments now need to account for assets they may not own in their overall continuity plans as well as their security plans. This is no small task, but ITPartners+ has the tools companies need to accomplish these goals.
Tip #10: Protect Against Cloud Data Loss

Companies are moving to cloud-based storage for good reason – it allows users to access important company information regardless of their location, which is a huge advantage for remote work. But many companies erroneously assume that simply because their data is in the cloud, it is safe and secure. While the likelihood of data loss is less with data in the cloud, it is still your organization’s responsibility to make sure the data is safe.
The concept of shared responsibility means that your cloud provider will take the responsibility for providing the infrastructure, perimeter security, and other tasks related to the availability of the platform, infrastructure, and software. It is the responsibility of the client organization to ensure the availability of their company data.
Here are some scenarios that will impact the availability of your cloud-based data.
- User error. End users are known to accidentally delete files. Sometimes those file or mailbox deletions won’t be noticed in time and the provided “Recycle Bin” functionality won’t suffice.
- Ransomware. If ransomware encrypts your cloud-based data, what will you do?
- Less likely, but Azure and MS365 do go down.
Conclusion
The advent of remote work means, by definition, that the network of 2019 is outdated and not suited for the new security and continuity challenges presented by a fragmented workforce. In order to ensure the availability and security of applications and data, IT departments need access to tools and processes that mitigate the new risks presented by today’s remote workers.

10 Tips To Help Keep Your Team Safe
- VPN
- Roaming DNS Filtering
- Secure Passphrase
- Multi-Factor Authentication (link to Duo landing page on ITP’s site)
- Password Manager (link to password manager blog on ITP’s site)
- WIFI Security
- End User Education
- Detect and Respond
- Business Continuity
- Shared Responsibility



